To make your life around cybersecurity simple and affordable.
As simple as that!

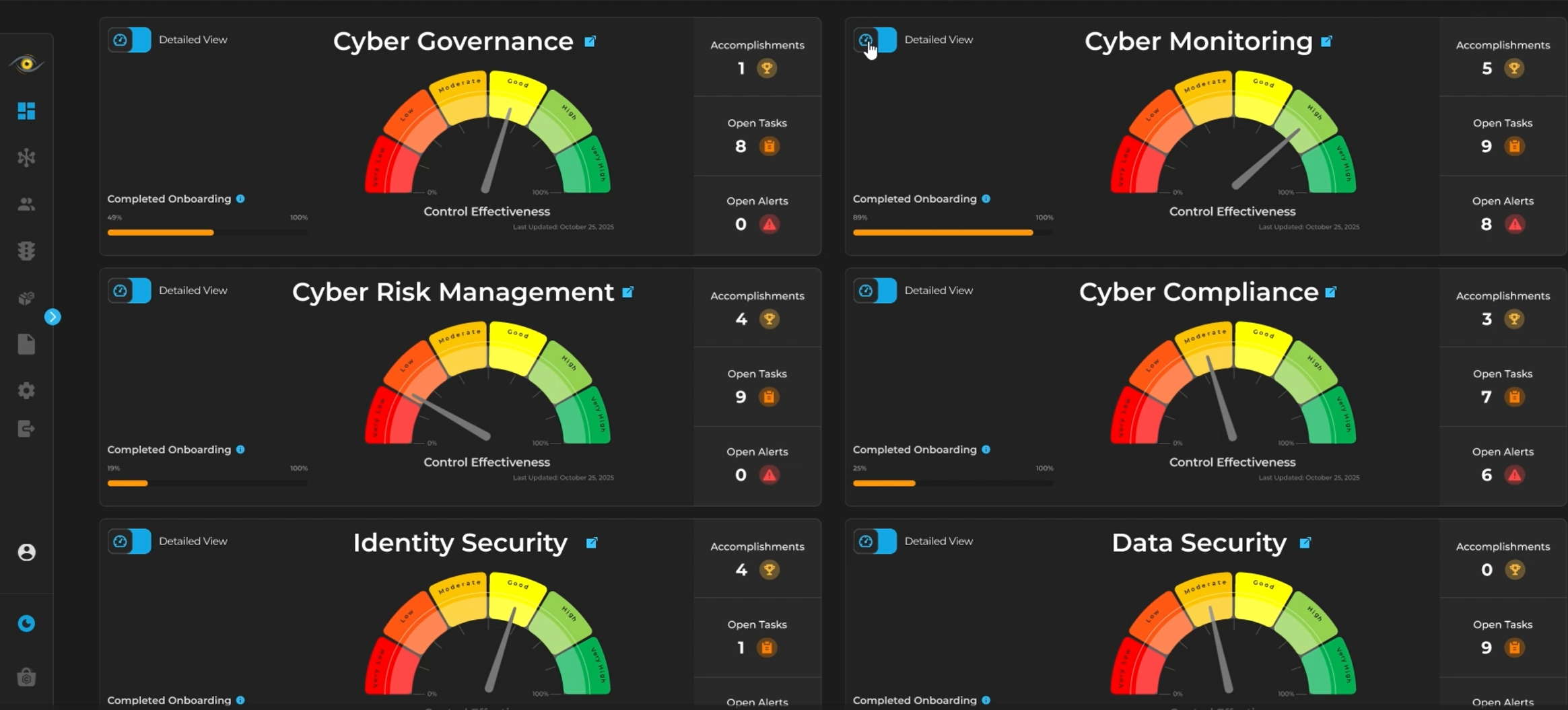
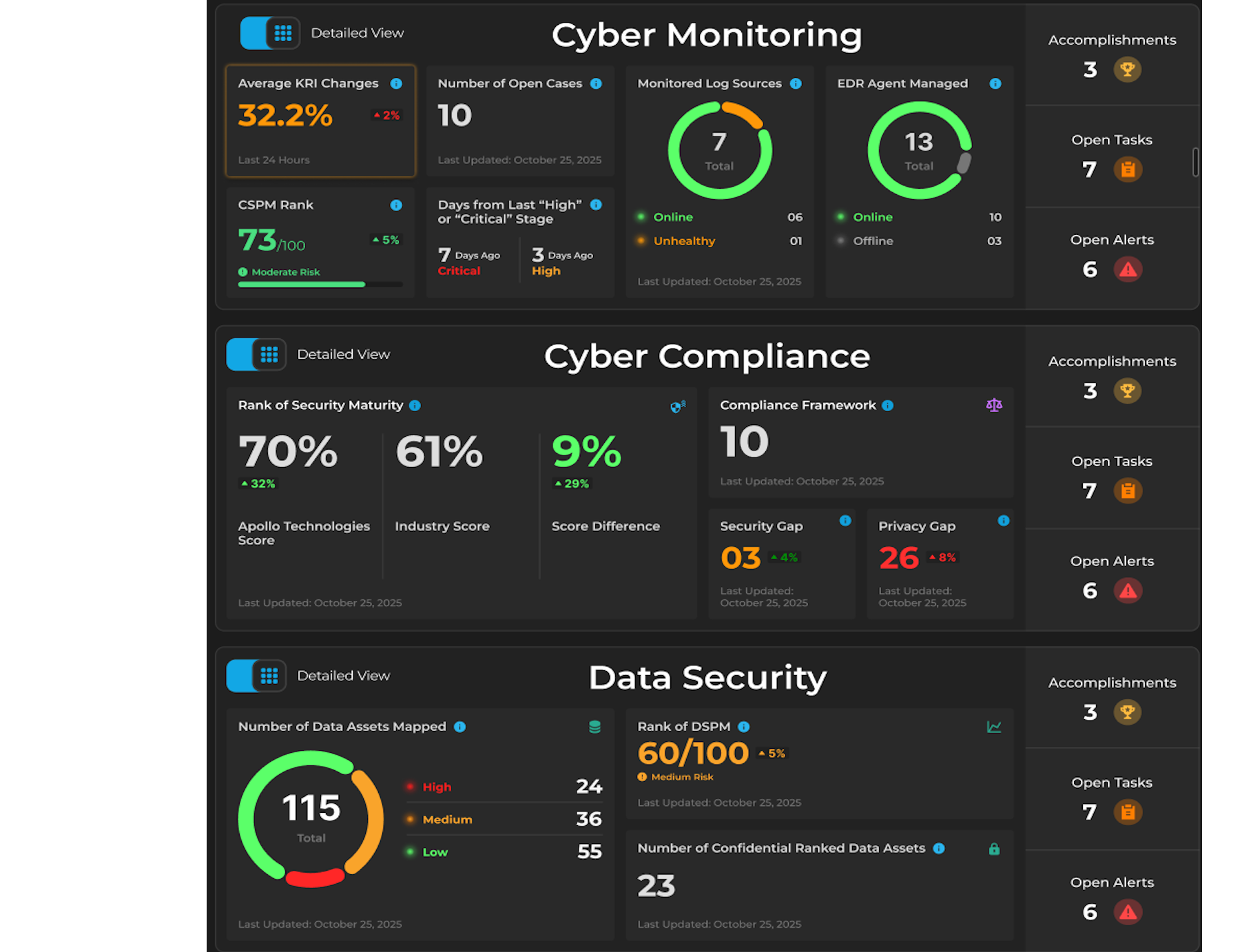
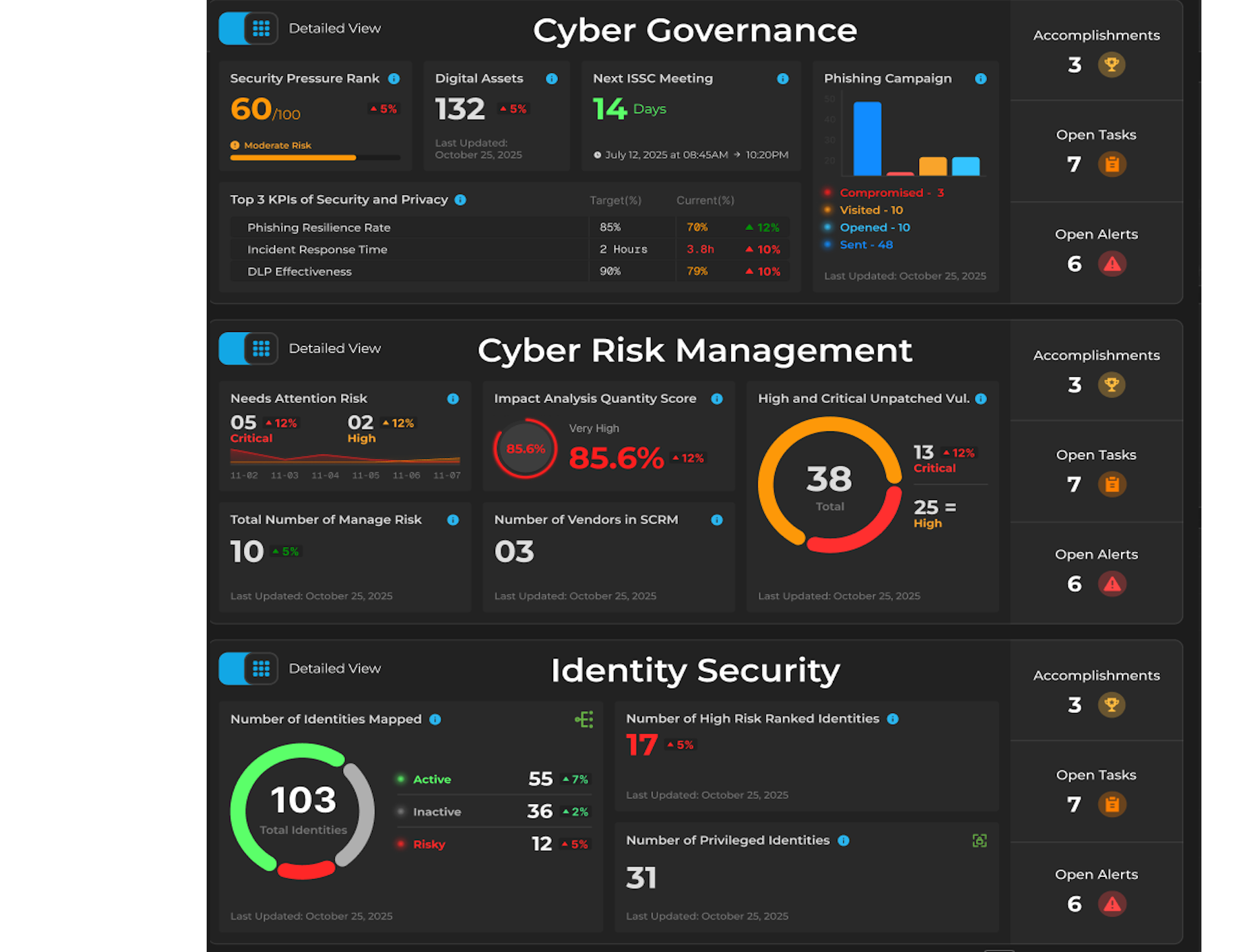
Interoperability between all six domains,
and 42 sub-domains of cybersecurity, enables efficient real-time decision making.
When an event occurs in one part of your business, it is instantly assessed for risk, prompting responsive actions in other areas that contribute to the broader cybersecurity landscape.

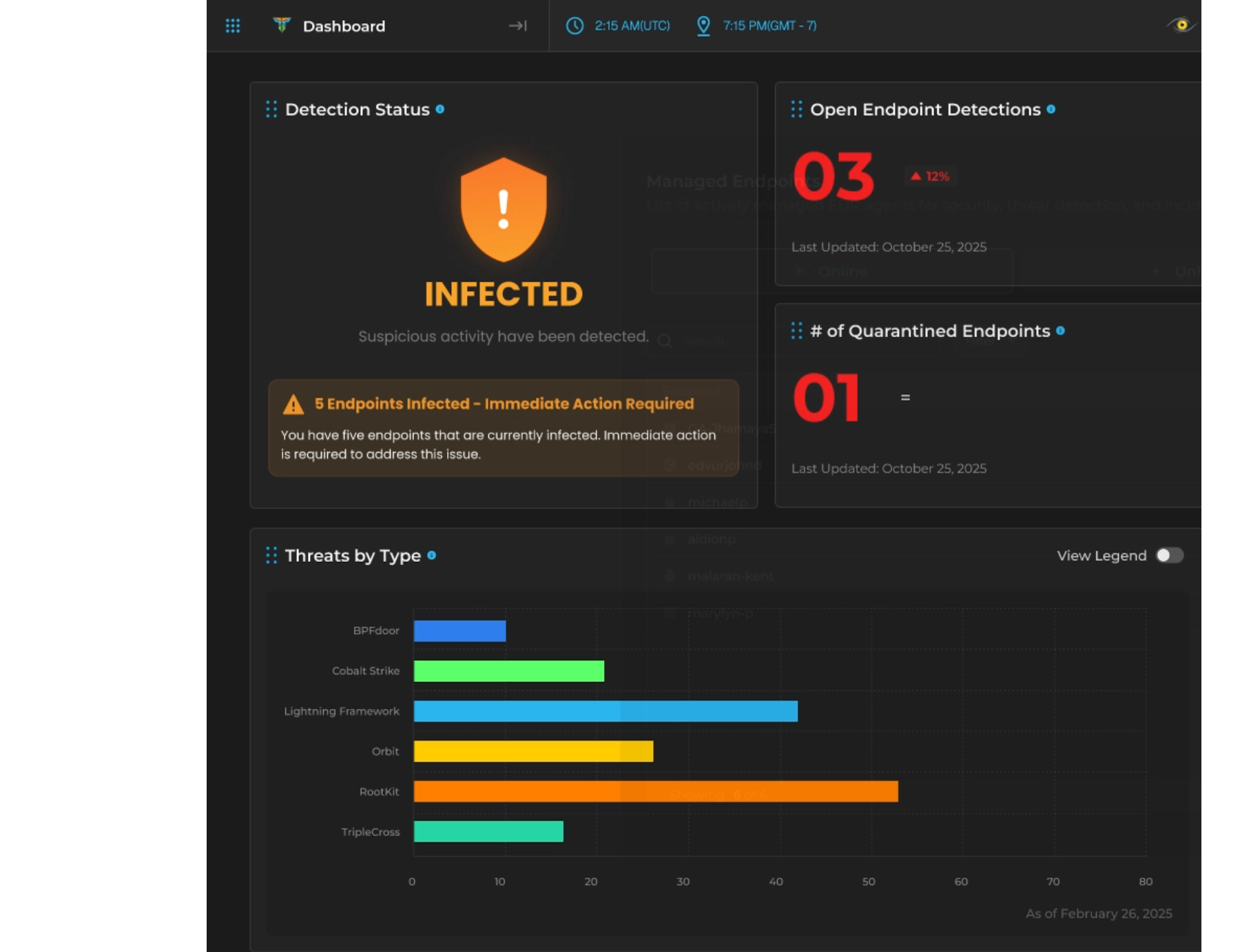
AQUILA embedded EDR likely enhances operational efficiency while maintaining high levels of protection across the enterprise.
Getting started with AQUILA is straightforward and efficient.
Deploy Log Collectors
Install log collectors within your organization to begin aggregating logs from various sources.
Integrate & Monitor
Follow the integration walkthrough to connect log sources to log collectors.
Once linked, AQUILA starts monitoring your critical digital assets.
Cloud Security Setup
Connect your cloud environment to AQUILA’s Cloud Security Posture Management (CSPM). AQUILA now begins analyzing users and entities for anomalies and security improvement opportunities.
CRAM Onboarding
Complete the Cyber Risk Assessment and Management (CRAM) onboarding to receive customized cybersecurity insights that align with your business needs.

That’s the power of AQUILA—taking the burden off your team so you can focus on what matters! With AQUILA’s cybersecurity operations center handling threat detection, response, and security optimization, businesses get proactive protection without the stress of constant monitoring.






















AQUILA is designed to streamline cybersecurity operations with a proactive and adaptive approach. This isn’t just another all-in-one platform for cybersecurity and privacy management—it’s a comprehensive solution that provides an unparalleled “eagle-eye” view of your entire cybersecurity landscape.
Think of AQUILA as a Swiss army knife, designed to tackle all aspects of cybersecurity challenges, from emergencies to routine operations. Whether you are detecting and responding to incidents in real time or preparing a management presentation on cybersecurity and privacy challenges, AQUILA addresses every aspect of your needs seamlessly.
AQUILA provides a comprehensive cybersecurity and privacy management framework, addressing over 99% of an organization's security concerns through six critical domains. These domains form a complete, interconnected ecosystem that enables businesses to effectively manage risk, maintain compliance, and ensure robust security operations.
CyTech ensures robust client data protection in AQUILA through a combination of compliance, security frameworks, and proactive monitoring. Here’s how:
- ISO 27001 & ISO 27701 Compliance: CyTech adheres to internationally recognized standards for information security and privacy management, ensuring structured safeguards against unauthorized access.
- Data Minimization & Transparency: AQUILA collects only necessary data and maintains clear communication about its usage, reinforcing trust and compliance with privacy laws principles.
- Security by Design: Privacy and security considerations are embedded into AQUILA’s architecture from the ground up, reducing vulnerabilities.
- Continuous Monitoring & Updates: CyTech actively monitors security protocols and updates them to counter emerging threats.
AQUILA not only simplifies cybersecurity management but also transforms the way complex processes are handled through its intelligent automation capabilities. Leveraging advanced AI and machine learning, the platform continually refines its algorithms to detect, analyze, and respond to cyber risks with precision. This ensures that even the most intricate tasks, which would otherwise require substantial manual effort or expert intervention, are executed seamlessly and efficiently.
AQUILA delivers transformative results in the realm of cybersecurity management, significantly optimizing the efficiency of your cyber-related operations. On average, organizations utilizing AQUILA experience a remarkable 60% reduction in time and resources dedicated to cybersecurity tasks. For some businesses, this figure climbs even higher, reaching savings of nearly 80% in both cyber labor and consultancy expenditures.
You can upgrade your AQUILA subscription at any time, adding features to enhance your experience. This reflects the value you see in AQUILA and your desire to maximize its benefits—aligning perfectly with our philosophy: achieve more with less. Less cost, less cybersecurity expertise required, and less complexity.
If you ever decide to downgrade your subscription after completing the cycle, it may indicate that AQUILA hasn’t fully met your expectations or that budget constraints are a concern. In either case, we encourage you to let us improve your experience—whether by enhancing value or addressing affordability—to ensure AQUILA works better for you.
Yes.
We offer 30% discount for annual subscription on all plans and features.
Interoperability: The Key to Unified Cybersecurity
AQUILA's standout feature is its interoperability, which allows different modules and functionalities within the platform to communicate and work together harmoniously. This ensures that cybersecurity operations are not siloed but rather interconnected. For example, when a phishing simulation is run to test and educate employees about recognizing cyber threats, AQUILA doesn’t stop at simply identifying who fell for the simulation. It goes a step further by marking these individuals as potentially high-risk users.
Dynamic Risk Identification and Monitoring
Once an individual is flagged, AQUILA automatically links this risk designation to the data, systems, and resources they interact with. For instance:
- Sensitive files or critical systems accessed by this individual may be tagged for closer scrutiny.
- Elevated monitoring protocols are applied to ensure proactive risk mitigation.
This dynamic risk profiling means that AQUILA doesn’t just react to incidents; it anticipates potential vulnerabilities by connecting user awareness (or lack thereof) with broader cybersecurity implications. This approach ensures that identity security, data security, and system integrity are all addressed in real time.
Real-Time, Intelligent Automation
What sets AQUILA apart is its ability to keep a constant, real-time pulse on your cybersecurity landscape. Its 24/7 monitoring capabilities mean risks linked to high-risk individuals, sensitive data, or critical systems are flagged immediately. This rapid response mechanism streamlines the workload for human analysts, who would typically spend significant time manually correlating such risks. For organizations without dedicated analysts, AQUILA’s automation fills the gap, enabling swift action without requiring additional resources.
Comprehensive System Responses
AQUILA’s integrated approach ensures that flagged risks trigger actions across the board. For example:
- Systems associated with a high-risk individual are assigned a higher risk status, prompting increased monitoring or restrictions.
- Automated workflows notify relevant personnel or systems to address the issue, ensuring no delay in response.
- Machine learning algorithms adapt in real time, enhancing the system’s future ability to predict and mitigate similar risks.
AQUILA is fully mobile-friendly, accessible through your web browser on any mobile device, just like a standard website.
Meanwhile, our Cyber Research and Development team is actively developing dedicated Android and iOS apps. These applications will expand functionality, empowering users to strengthen their cybersecurity efforts directly from their mobile devices.
AQUILA undergoes frequent updates to ensure its cyber operational features remain at the forefront of security. All technological components receive updates at least twice daily, including new Indicators of Compromise (IOCs) that enhance AQUILA’s ability to detect emerging cyber threats in real time.
For managerial aspects such as Security and Privacy Compliance, Risk Management, and other non-technical components, updates follow a structured two-week cycle. For example, when new cybersecurity regulations or privacy laws emerge, our compliance research team analyzes the changes and collaborates with the development team to implement necessary adjustments in the Cyber Compliance domain. After thorough testing and verification, these updates are deployed into AQUILA’s production environment, typically within two weeks.
AQUILA, in most of its parts and features, is fully customizable to support the wide range of users we have worldwide. AQUILA, being your right hand now in all aspects of cybersecurity, needs to work for you, not the other way around. This means that our development team is working hard to make it easy for you to use, customize, and excel your cybersecurity.